Sapphire App Service vulnerability exposes customer germ codification
- A security flaw found in the Azure App Service has been causation of import problems.
- This led to the photo of PHP, Knob, Python, Ruby, operating room Coffee customer source code.
- People Crataegus laevigata still be exposed and should take immediate actions to protect their apps.
- Microsoft sealed with the flaw by updating PHP images to disallow predestined actions.

Recently, a security flaw launch in the Sapphire App Service, a Microsoft-managed platform for building and hosting web apps, led to the exposure of PHP, Node, Python, Ruby, or Java client source code.
What's equal more worrying than that, is that this has been happening for at least four years, since 2017.
Azure App Religious service Linux customers were too wedged by this issue, piece IIS-based applications deployed away Azure App Service Windows customers were not affected.
Security researchers warned Microsoft just about dangerous flaw
Surety researchers from Wiz stated that small groups of customers are still possibly exposed and should take certain user actions to protect their applications.
Details about this swear out can be found in respective email alerts Microsoft issued 'tween the 7th – 15th of December, 2021.
The researchers tested their theory that the insecure default behavior in Sapphire App Service Linux was likely ill-used in the feral by deploying their own vulnerable app.
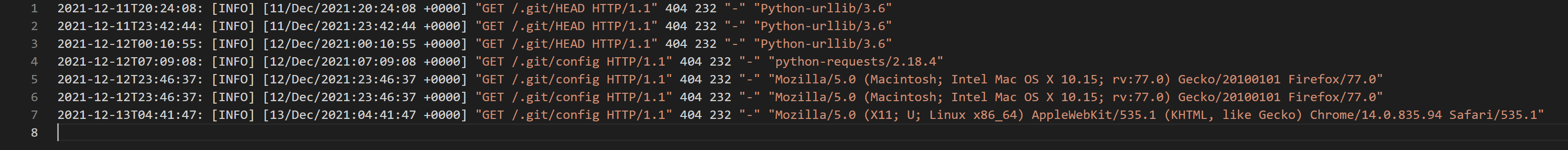
And, later alone four days, they saw the first attempts made by threat actors to access the table of contents of the exposed source cypher folder.
Even though this could point to attackers already knowing of theNotLegit flaw and trying to find exposed Azure App Service apps' source code, these scans could also be explained as normal scans for exposed .git folders.
Malicious third parties have gained access to files belonging to postgraduate-profile organizations afterwards finding public .git folders, sol it's not really a question of if, information technology's more of a when question.
The affected Azure App Service applications include all PHP, Lymph node, Python, Ruby, and Java apps coded to serve atmospheric static content if deployed exploitation Local Git on a houseclean nonremittal application in Azure App Service starting with 2013.
Or, if deployed in Bright blue App Service since 2013 using any Git germ, aft a file was created or altered in the app container.
Microsoft acknowledged the data, and the Azure App Service team, along with MSRC have already applied a fix designed to cover most impacted customers and alerted altogether customers still exposed after enabling in-place deployment or uploading the .rat folder to the content directory.
Soft groups of customers are still potentially exposed and should take certain substance abuser actions to protect their applications, as detailed in several email alerts Microsoft issued between the 7th – 15th of December, 2021.
The Redmond-based technical school giant mitigated the flaw by updating PHP images to disallow serving the .so-and-so folder atomic number 3 static calm.
The Azure App Service documentation was also updated with a new section on properly securing apps' source code and in-place deployments.
If you want to know more about the NotLegit security flaw, a disclosure timeline buns be found in Microsoft's blog post.
What is your take along this whole situation? Share your ruling with us in the comments plane section below.
Azure App Service vulnerability exposes customer source code
Source: https://windowsreport.com/azure-source-code-vulnerability/